The purpose of this article is to present a framework and a method for cyber-target categorization. The framework contains factors, which influence on cyber targeting process and the presented categorization method provides an example, how cyber-targets could be categorized to support targeting decision making.
The article is based on literature study. Research method was to build an analogy between conventional and cyber targeting.
Cyber targeting does not seem to be studied widely, but the common approach to cyber security seems to be “threat-based”. This article presents a new categorization criteria and method for cyber-target analyze, with a target-based approach.
1 Introduction
Importance
Targeting is an important component of the effect-based warfare. According to AFDD (Air Force Doctrine Document) 3-60 targeting during conflict enables air and space power to be a decisive force in modern warfare [1]. In effect-based cyber warfare, targeting is as needed component as in conventional warfare. In cyber warfare, there is a clear difference between targeted operations and “pointless” use of malware.
Conventional targeting is the process for selecting and prioritizing targets and matching appropriate actions to those targets to create desired effects that achieve objectives, taking account of operational requirements and capabilities [1]. Structured target analysis can support targeting process to achieve commander’s objectives. In this article, target analysis means basically target categorization for the targeting process. The objective of the target analysis is to identify both valuable and available targets.
Research method
The objective of this article was to create new criteria for categorizing cyber-targets. The research question was: How cyber-targets should be categorized to support targeting. The research method was to build an analogy between conventional and cyber targeting. Method considered comparison between conventional and cyber: targeting, infrastructure, weaponeering and target.
The main result of the research is a proposal about the criteria for cyber-target categorization. The results of the research can be used in cyber targeting process. Additionally the presented methodology can be used to improve cyber security.
Research framework
The research question was divided into sub questions as follows:
- What is the framework for cyber targeting?
- Which factors influence cyber targeting?
- Which are the essential features of the cyber-targets considering effect-based targeting process?
In the article, the conventional targeting process was examined to provide the base for the analogy. Then the different approaches for evaluating target value and availability were examined. Previous research related exactly to cyber targeting was not available. However there were supporting research about, cyber security, cyber weapons and cyber warfare. The approach to the literature study is presented in Figure 1.
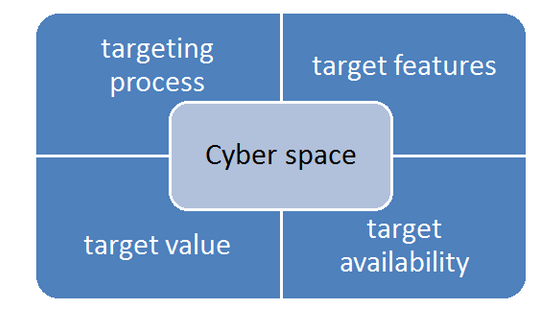
Figure 1. The approach to the literature study. The conventional targeting process is examined in cyberspace. Approach considers cyber-target features, cyber-targe tvalue and cyber-target availability.
2 Targeting process and target
Background
Targeting is the key element of effect based warfare. If the commander wishes to produce the maximum effect with minimal effort, targets have to be chosen carefully. If the commander uses his/her power like in Verdun, for example, enormous resources can be used and lostwithout gaining any advance. Beside the desired effect, careful targeting facilitates avoiding collateral damage against civilian targets while executing military operations. Targeting process can to be used in both cyber warfare as in conventional war to pick up the most suitable targets.
According to AFDD 3-12, the cyber tasking order is analogous to an air tasking order [2]. In cyber warfare, the role of targeting is actually emphasized compared to conventional targeting, as the cyber weapons are more target sensitive than conventional weapons. For example, a mortar can cause damage both against armoured or unarmoured targets, but a Windows operating system exploit can be totally useless in Linux environment.
Targeting process
In this article, targeting process is examined with US Air Force Targeting Doctrine Document and FAS (Federation of American Scientists) JCS Joint Publications related to targeting.
Targeting process is systematic evaluation of potential target systems and their components to determine which elements of the target system(s) should, or could, be taken against to achievethe given objectives [3]. The end product of the target development process is an unconstrained prioritized list of potential targets. It reflects relative importance of targets to the enemy's ability to wage war. This list of targets is the basis for the weaponeering phase, where own capabilities are evaluated against the suitable targets [3].
Joint targeting cycle contains six different phases. In the first phase, the strategic level objectives are established. The second phase contains the target development, vetting, validation, nomination and prioritization phase. In this phase, the potential target systems are systematically examined. In the third phase, own capabilities against desired effects are evaluated. In the fourth phase, commander makes decision and approves the target list. In the fifth phase, missions are planned and the final phase considers assessment [1].
One important notice about the targeting cycle is that it is iterative and the following phase may have an influence onthe previous one [1]. The cyber tasking cycle, which is based on the air tasking cycle, is also an iterative process [2].
Most of all, targeting process needs information about the possible targets. One absolute demand for any target isthat the target has to be available for reconnaissance. If the target cannot be evaluated in advance, or the effect on the target cannot be observed, the target should not be nominated at all.
Target characteristics
Targets are evaluated and categorized with target characteristics. Every target has certain characteristics, which form the basis for the target detection, location, identification, and classification for future surveillance, analysis, strike, and assessment. In general, there are four categories of characteristics by which conventional targets can be defined: physical, environmental, functional, and cognitive [1].
The physical features key characteristics of the target are: shape, appearance, number and nature of elements, reflectivity, structural composition, degree of hardening, electromagnetic radiation, location, size and dispersion. An example about environmental characteristics is terrain features. Cognitive features are, for example: how the target processes information, information that target requires to function, outputs to the processes the target performs, how much information the target can handle and how the target or system stores information. Functional features are, for example, what materials or resources the target requires to function. [1]
Converting physical and environmental characteristics into cyber space can be done by transforming them into virtual characteristics and IT infrastructure features. Physical characteristics would transform into cyber target's virtual characteristics, such as operating system, needed CPU efficiency, needed memory size and file or data formats. Cyber-target may also have an interface to physical space, which allows attacker to penetrate into cyber-target system through a physical connection. Environmental characteristics would consider network characteristics such as network protocols, layers, servers’ operating systems and databases – in otherwords the IT infrastructure characteristics.
Functional characteristics consider what the cyber-target does. For example, these characteristics would be target's mobility, ability to defend and reconstitute it. These characteristics are quite similar between the cyber-target and conventional target. Cognitive features are, for example, how the target processes information, process input and output and how the target stores information. [1] Overall physical and environmental characteristics have to be transformed into virtual characteristics and the functional and cognitive features are very similar inthe physical or cyber space. The analogy between physical and cyber characteristics is illustrated in Figure 2.
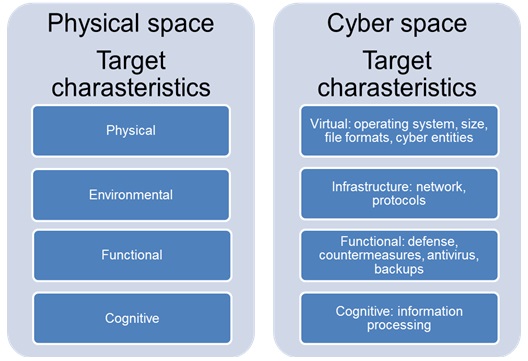
Figure 2. Analogy between conventional and cyber-target characteristics.
Weaponeering
Weaponeering means basically choosing the most effective and suitable weapon against the chosen target. Weaponeering can be seen as certain kind of optimisation. Some of the modern weapons are expensive and should be used after careful consideration. To be effective, targeting process must identify the best weapon for the intended target with appropriate timing to meet the objectives established by the commander. Weaponeering determines the quantity, type, and mix of lethal and nonlethal weapons required to achieve a specific level of target damage. [3]
Cyber-weaponeering itself is very target sensitive. Software exploits are useful only against certain vulnerabilities and totally useless against other cyber-targets. However, some cyber-attack methods, like denial of service attacks, can be used against several target systems.
Examples about cyber weapons and cyber-attacks against SCADA (SupervisoryControl and Data Acquisition) systems are [4]:
- Denial of service attacks tocause system shutdown.
- Deleting system files to cause system shutdown. Attack may not be avoided by reboot.
- Taking control of SCADA system. With this type of attack, an attacker may cause several kind of damage.
- Changing data in SCADA system.
3 Target Value
Concept
Target value means, how important the target is for the enemy's functionality. The reason for target value evaluation is that the attacker is able to choose those targets, which will cause the whole target system to collapse, after destroying the chosen targets. In conventional warfare, enemy commanding and communications functions are commonly seen as valuable targets. On nation level, critical infrastructures can also be seen as very high level targets. Protection of critical infrastructure such as water, power and energy is vital, because of the impact the destruction of the critical infrastructure would cause [5].
As the defender wants to protect the softest and critical targets, attacker wants to find and destroy the same targets. Because of this, both the attacker and defender can use similar analyse methods to find the critical points. The more critical the target is, the more valuable it is for targeting.
Network theory approach
In network theory approach, the critical infrastructure is modelled as a network to identify the critical nodes and links. Scale-free network theory establishes a basis for vulnerability analysis, because it reveals concentrations of assets that may be vulnerable for an attack. [5]
With the network theory approach, the most critical nodes or links can be identified in thecritical infrastructure. If the attacker manages to effect on these critical points, the whole critical infrastructure may be paralyzed with minimal effort. Network theory approach is suitable also for the defender. As the attacker wishes to find and destroy the critical nodes, defender can try to protect, harden, duplicate etc. the critical nodes and links to increase the security.
Systems theory approach
Systems theory approach can be used after or beside the network analysis. Systems theory approach provides information on how complex systems interact with their environment, and this guidance can be applied to designing security. With systems theory approach, security designers are able to build layered defence on the target system [6]. The goal of the security is to ensure the critical functions. With systems theory approach, instead of identifying the threats in the system, losses are identified. The question is, what essential services and functions must be secured against disruptions and what are the unacceptable level of losses. [7]
With systems theory approach, the control, input, output and components in the target system are identified [6]. By totally destroying control or one of these functions, the whole system may be paralyzed with minimal effort. Besides the control, every function is essential for the output of the process. Process can be destroyed also by destroying a single function or by producing enough damage for every function.
Effect on target network or system
When evaluating target value and the effect on the target system, target’s importance for the target system or target network has to be studied, as the importance differs between critical components. In causality model, an initial component failure cascades through a set of other components [7]. Cascade failures are system-wide failures that begin with on single failure, but propagate throughout the entire system or network, ending in calamity [5]. With cascading effect, paralysing a single node, link of function, the whole target system or target infrastructure can be damaged. To avoid collateral damage and other unwanted effects, which cascading effect may cause, the meaning and functionality of the chosen cyber-target has to be known in advance.
Other target value characteristic may be target’s capability to recover from the attack. For example, denial of service attack may not cause any permanent damage. Business systems may recover from an attack by simply rebooting the target system. But, for example, in industrial control systems reboot cannot beused as easily to solve problems as in enterprise environment [8]. Rebooting a SCADA system may cause the shutdown of the power plant of production facility, which cannot be done without preparations.
On the other hand, fault-tolerant networks continue to function even when some of the nodes or links do not operate [5]. An attack against a single critical component in the fault-tolerant system, can be totally useless for the attacker.
Levels of the cyber target
In cyberwarfare research, cyber targets seem to be discussed only on very high level – as large infrastructure targets or whole information systems, or the concept of cyber target is not deeply analysed.
The chosen method to analyse a critical infrastructure or a target system influence on the targeting process. For example, a target system can be seen as a group of potential cyber-targets for the targeting process. According to Federation of American Scientists, military targets may be further classified as strategic, operational, and tactical [3]. While planning a cyber-attack, the target cannot be examined on system or network level, but the target system has to be divided into target and target entity levels. This is similar in conventional warfare as an anti-tank weapon can fire against a single tank, but not the whole tank division.
Cyber-target may be divided into different categories based on the level of the target. The highest level of the cyber-target concept would be cyber-target system, which is formed from the subsystems, and is the main objective of the attack. This could be, for example, SCADA or a flight control system. Cyber-targets would be single functions and subsystems, which are needed to make the whole system to function.
Cyber-target entity is a part of cyber-target which can be destroyed individually, but it is essential for the target system to operate. Cyber-target entity could be a single process, file, a sensor or a single function. Cyber-target entities are autonomous with simple behaviours and connect together and form a service. The levels of cyber-target are illustrated in Figure 3. For effect based warfare, it is essential to choose the correct target entity in the correct target system.
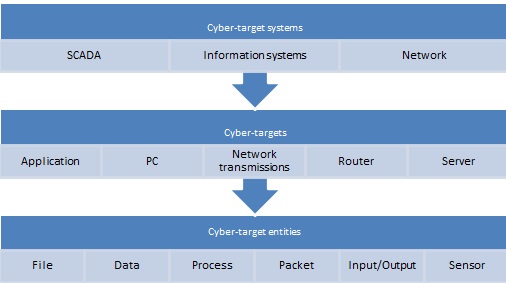
Figure 3. Levels of the cyber-target
On cyber-target system level, possible systems could be SCADA or other information systems, network and network communications or organizations IT-infrastructure containing, for example, data storages, office software and identity handling systems. SCADA is a system to automate industrial control and monitoring [8]. SCADA systems are composed of computers, network communications, sensors, remote units and programmable logic controllers [5]. The complex and distributed structure of SCADA creates several attack vectors against it.
Cyber-target system can also be a hybrid, which exists in both in the cyber and the physicalspace. With a cyber-target system, an end user can also be influenced through the system, even when he/she does not exist in cyber space, or the target maybe a physical device.
The ultimate objective of a cyber-attack may locate in the physical layer of thecyber space, or it may be the human actor above the application layer, or it may be inside the cyber space itself.
4 Target Availability
Concept
Target availability means how easy the target is to reconnoitre and destroy. The basic method for target availability analysis is to divide targets to “soft” and “hard” targets.
The actual target analysis can be carried out using several methods. Because the decision making process is constrained by time, costs, previous experiences, and perceptions of the participants, a great deal of decision making in the target development arena is based on qualitative rather than quantitative analysis. However, qualitative analysis is not a substitute for quantitative analysis. Both are useful techniques for structuring a problem to reach a rational conclusion. Both may be used to reduce uncertainty in decision making.
The keyelements of the target availability are: 1) target defence and 2) target vulnerability.
Cyber-target system defence contains [4,6,7,8,11]:
- Access control (firewall for example)
- Anti-malware
- Encryption
- Intrusion detection systems
- Backups and mitigation
- System hardening
- Honeypot to distract the attacker
Cyber target vulnerability can be evaluated with CIA (information confidentiality, integrity and availability) approach. With this approach the information isseen as a target and the objective is to influence on the 1) information confidentiality by revealing secret information, 2) information integrity by removing or alternating information or 3) information availability by denying users to gain access to desired information.
Cyber weapon target analysis
In cyberweapon target analysis, the cost of achieving the target is evaluated withcertain criteria. With cyber weapon systems, the cost of achievement analysisis conducted by considering the cyber weapon system functions and thecomponents of the cyber-attack, to gain the overall understanding about thechosen cyber-target system. The evaluation should consider:
1) Possibility for the initial penetration into target’s cyberspace.
2) Possibility to operate in the cyber-target system containing:
a) Searching
b) Identifying
c) Spreading
d) Connecting to C2 servers
e) Communications with peers
f) Evaluating the situation
3) Possibility to influence the cyber-target and cyber-target entity.
4) Possibility to evaluate the caused effect on the cyber-target system.
5) Possibility to avoid cyber-target system's countermeasures.
For a successful attack, the cyber weapon system has to be able to perform all these actions. [9]
5 Target reconnaissance
Concept
Reconnaissance attacks allow an attacker to identify potential cyber-targets in advance [10]. To be able to gather all the information needed for the targeting process, the cyber-target has to be easy enough to reconnoiter. If the target system is a ”black box” and there is no information available about its functionality and features, the target can be seen as very hard target to influence.
Public information
Public information means information which is legally available for anyone. Some of the target system information may be online and available for anyone through the internet. Software and hardware manufactures usually provide documentation and other online information about their products. Information may contain, for example, default passwords and configuration. Inquiring public information is legal and can be done with home PC through internet.
Network devices can be seen as easier targets for reconnaissance, because the documentation is usually available in the internet. For example, information about SCADA systems, programmable logic controllers etc. can be found from online documentation available for anyone [4].This makes them possible critical infrastructure targets, because control systems security is of prime importance for example for energy sector [8].
Public information may be easily inquired with, for example, search engines. If the device type and serial number are known, critical information about cyber-targets features and functionality can be found easily. Additionally the usage of common technologies, such as TCP/IP and common operating systems, makes the target systems easier to reconnoiter [4].
Hidden information
In this article, hidden information means information, which is not publically available. Revealing hidden information is usually illegal or revealing it requires illegal methods and tools. Usually the search of hidden information is done after all the public information is already gathered. Methods for searching hidden information can be technical or social engineering.
Usually the search of hidden information requires more sophisticated software tools and skills than the search of public information. Attacker has to be able to use tools like Netcat, Nessus and NMAP, and he/she has to be able to evaluate the results.
During reconnaissance attackers identify systems and then finger print the connected systems. Finger printing means finding out which ports are open and identifying version of the remote operating system [10, 11].
Social engineering means obtaining hidden information using human vulnerabilities. There are various techniques to commit social engineering. One of the effective features with social engineering is, that target may not even realize being under reconnaissance. [12]
6 Conclusion
Based on the approaches presented in the chapters 2, 3, 4 and 5, it is possible to build a categorization method for evaluation cyber-targets for cyber targeting process. The factors influencing on target categorization are presented in Figure 4 and the proposal for the cyber-target categorization is presented in Table 1.
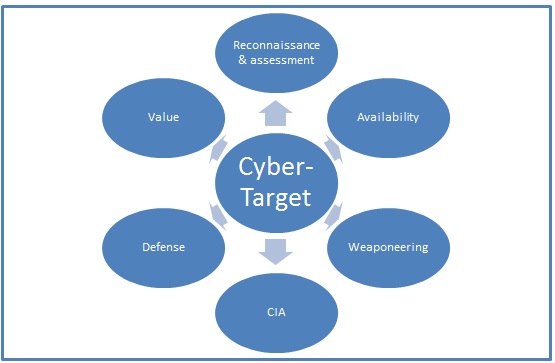
Figure 4.Target categorization criteria.
First of all, targeter has to be able to reconnoitre the cyber-target. The easier it is to gain information about the target, the easier it is to analyse the target. One important notice is, that also the effect on the target has to be assessed. Cyber-targets using common commercial software and hardware and common protocols can be inquired more easily than “black box” or legacy systems, which have old and tailored software, which may not be well documented. Hiding information is not an inclusive solution, because there are methods for revealing hidden information technically or with social engineering.
With target analyse, there has to be a clear understanding about the levels of the target. Target value has to be examined based on the effect on the system or infrastructure level. After the cyber-target system is chosen, targeter has to identify the critical targets inside the target system. After identifying the targets, targeter can choose the correct cyber-target entities to be affected. Good features for the target are possible cascading effect and poor capability to recover.
Availability means that attacker is really able to affect the valuable target. Attacker has to be able to connect to target’s cyber space. Internet access makes target systems easier to attack, when there is no need for physical connection. Remote connections enable attacks from the distance without entering to the target system area geographically.
Good target defence can prevent the attack in advance. If the target systems has reliable access control and intrusion detection system, it decreases attacker capability to operate in the target system. Encryption can hide critical information and possible use of honey pots create contingency for the operation.
Weaponeering is highlighted in cyber-attack. Cyber weapons are much more target sensitive than conventional weapons. Exploits are useful only against certain vulnerabilities. For the weaponeering, targeter has to gain a great deal technical information, such as operating systems, software versions, updates and configuration – in other words information about target’s characteristics.
After all, the final objective is to influence a cyber-target entity. Target entity’s information has to be affected and one or several tenets of target’s CIA must be compromised. For this objective, target-entities’ features must be known. Cyber-target entity has to be chosen carefully. Influencing right entity in the wrong system or vice versa, makes an attack ineffective. Information needed about cyber-entity contains the nature of the entity, environmental features such as operating system and protocols and hardware.
| Cyber-target | |
| Reconnaissance | White box vs. Black box |
| Value | Critical vs. easy to replace |
| Availability | Available vs. unavailable |
| Target defence | Soft target vs. hard target |
| Weaponeering | Suitable weapons considering target characteristics |
| CIA | Cyber entity features |
Table 1. Categorization method for cyber-targets.
7 Discussion
The role of targeting seems to even increase in cyber warfare compared to conventional targeting. Cyber weapons can be totally useless in wrong kind of virtual environment and cyber-weaponeering is very target sensitive. There is a clear difference between targeted attack and “pointless” use of malware. Targeted cyber operations save resources, increase results and reduce collateral damage.
The conventional targeting process is a suitable approach also with cyber targeting and similar functions can be used with cyber-targets, but the importance and signification may differ. For example, available weapons influence a great deal on which target characteristics are important to reveal. On the other hand, cyber weapons can also be manufactured faster than conventional weapons and found opportunities may be more easily exploited.
There seems to be several methods for defender to turn his/her system as a “hard” target and avoid the attack in advance. These methods consider reducing single targets value and availability. The most useful defence method could be layered defence, where the first step would be hiding the systems existence, functionality and characteristics.
This article bases on literature study and presents only a proposal about cyber-target categorization. Presented criteria for cyber-target categorization should be evaluated in future research. Especially the weight of each presented categorization criteria, should be evaluated during an actual cyber-targeting process.
References
1 Air Force Doctrine Document 3-60, Targeting, United States Air Force, 2006, 2011. http://www.fas.org/irp/doddir/usaf/afdd3-60.pdf cited 21.4.2014
2 Air Force Doctrine Document 3-12, Cyberspace Operations, United States Air Force, Cyberspace Operations, 2010, 2011. http://www.fas.org/irp/doddir/usaf/afdd3-12.pdf cited 1.5.2014
3 Federation of American Scientists, JP 3-55, Reconnaissance, Surveillance, and Target Acq Sppt for Joint Op, 1993. https://www.fas.org/irp/doddir/dod/jp3-55/3-55ch4.htm cited 1.5.2014
4 Pollet, J, Developing a Solid SCADA Security Strategy, Published in Sensors for Industry Conference, 2nd ISA/IEEE, pp 148–156., 2002
5 Lewis, T, Critical infrastructure protection in homeland security, John Wiley&Sons, Inc., Hoboken, New Jersey, 2006
6 Concling, A,&Dietrich, G, Systems theory model for information security, Published in Hawaii International Conference on System Sciences, Proceedings of the 41st Annual, pp 265., 2008
7 Young, W,&Leveson, N, G, Inside Risks and Integrated approach to Safety and Security Based on Systems Theory, Published in Communications of the ACM, Feb2014, Vol. 57 Issue 2, pp 31-35., 2014
8 Mahboob, A,&Zubairi, J, Intrusion Avoidance for SCADA Security in Industrial Plants, Published in Collaborative Technologies and Systems (CTS), 2010 International Symposium, pp 447-452., 2010.
9 Hakkarainen, P, Cyber Weapon Target Analysis, Book on Demand, 2014
10 Morris, T,H, Shengyi, P,&Adhikari, U, Cyber security recommendations for wide area monitoring, protection, and control systems, Published in Power and Energy Society General Meeting, IEEE, pp 1-6., 2012
11 Rowe, N,C,&Goh, H,C, Thwarting Cyber-Attack Reconnaissance with Inconsistency and Deception, Published in Information Assurance and Security Workshop, IAW '07, IEEE SMC, pp 20-22., 2007
12 Mouton, F, Malan, M,M, & Venter, H,S, Social Engineering from a Normative Ethics Perspective, Published in Information Security for South Africa, pp 1-8., 2013